...
| Code Block | ||||
|---|---|---|---|---|
| ||||
export ADMIN_TKN=$(curl -s -X POST --insecure https://$HOST:$KEYCLOAK_PORT/auth/realms/master/protocol/openid-connect/token \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "username=admin" \
-d 'password=admin' \
-d 'grant_type=password' \
-d 'client_id=admin-cli' | jq -r '.access_token')
echo "ADMIN CLIENT TOKEN = $ADMIN_TKN"
curl -X POST --insecure https://$HOST:$KEYCLOAK_PORT/auth/admin/realms/x509provider/clients \
-H "authorization: Bearer $ADMIN_TKN" \
-H "Content-Type: application/json" \
--data \
'
{
"id": "x509Client",
"name": "x509Client",
"enabled": "true",
"defaultClientScopes": ["email"],
"redirectUris": ["*"],
"attributes": {"use.refresh.tokens": "true", "client_credentials.use_refresh_token": "true"}
}
' |
Keycloak SSO & User management
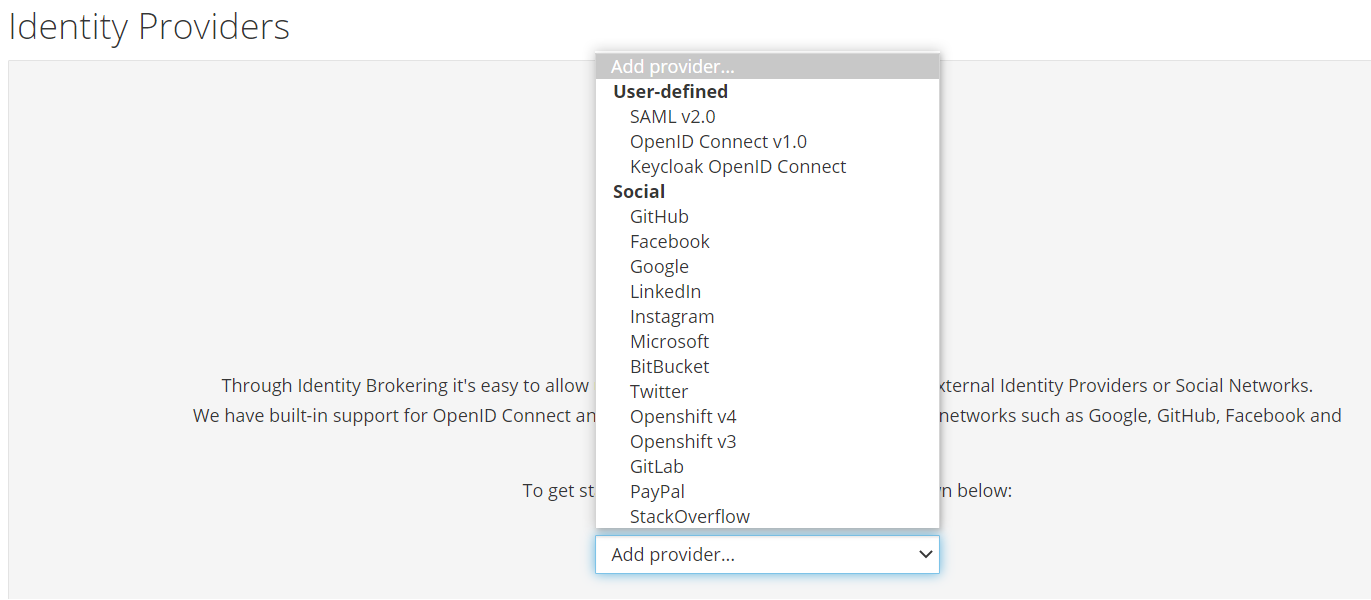
Identity Providers
You can use keycloak for single-sign so users don't have to login to each application individually.
You can also use external identiity providers such as google or github if required.
See the "Identity Providers" menu in the keycloak UI.
User Federation
You can also use existing LDAP, active directory servers or relational databases for user management if this is required.
Open Source Identity and Access Management
See the "User Federation" menu in the keycloak UI.