This page is out of date.
Please see the relevant page for the latest release: e.g. Release J - Run in Docker
network policy is used to control the traffic flow between endpoints in k8s cluster.
This is a brief instruction on how to apply network policy to NONRTRIC. This page deploy NONRTRIC and apply a simple network policy to it.
Prerequisite
- Docker
- minikube v1.22.0
- cilium v1.10.2
Installation
configure minukube resources, the NONRTRIC deployment may cost more resource than default settings in your env:
minikube config set cpus 4 minikube config set memory 16384
start minukube and enable network plugin:
minikube start --network-plugin=cni
install network plugin, eg: cilium
download cilium and run command, it will detect the minikube cluster automatically and install the network plugin in the cluster:
cilium install
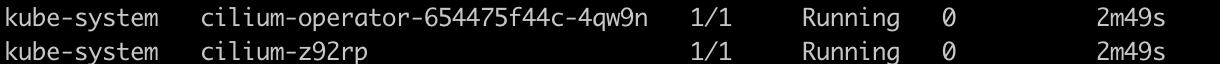
After successful installation, we should see the pods:
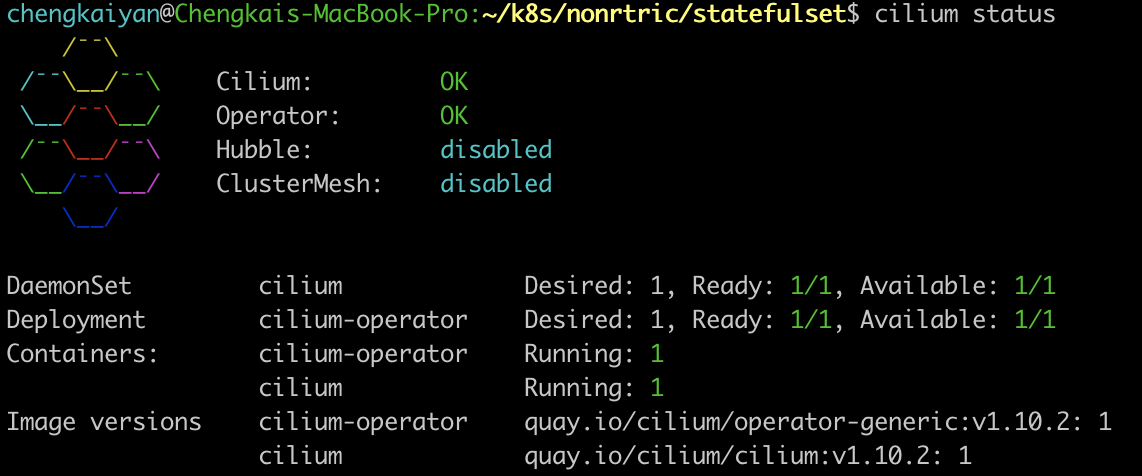
Check cilium status:
cilium status
Now we have network plugin enabled in k8s cluster, we can then apply network policy to NONRTRIC.
Deploy NONRTRIC
kubectl apply -f https://raw.githubusercontent.com/yanhuanwang/k8s/master/statefulset/nosdnc.yml
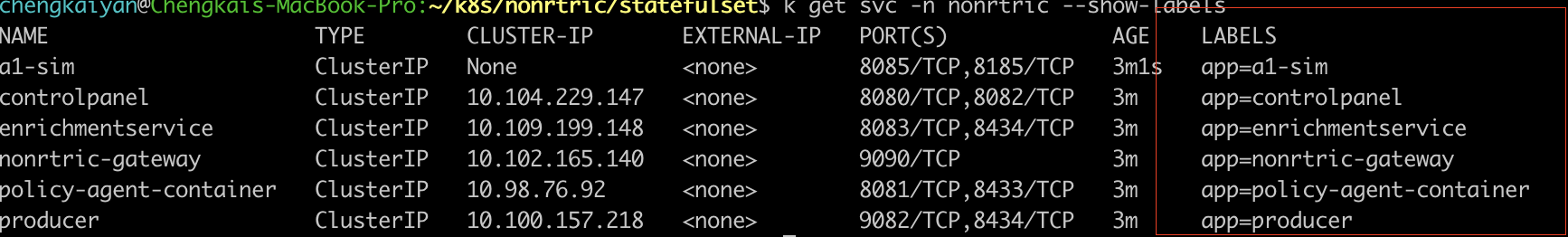
after deployment, you should be able to see nonrtric services/pods are up and running:
pay attention to the labels above, in this demo we will use labels to define the network-policy rules.
Apply network-policy
$ cat <<EOF | kubectl apply -f -
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: nonrtric
spec:
podSelector:
matchLabels:
app: a1-sim
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
app: policy-agent-container
- from:
- podSelector:
matchLabels:
app: a1-sim
EOF
The example policy above applies a rule on endpoint with lable "a1-sim", it only allows traffic coming from pod with labels "policy-agent-container" and "a1-sim".
Feel free to change the labels and apply it.
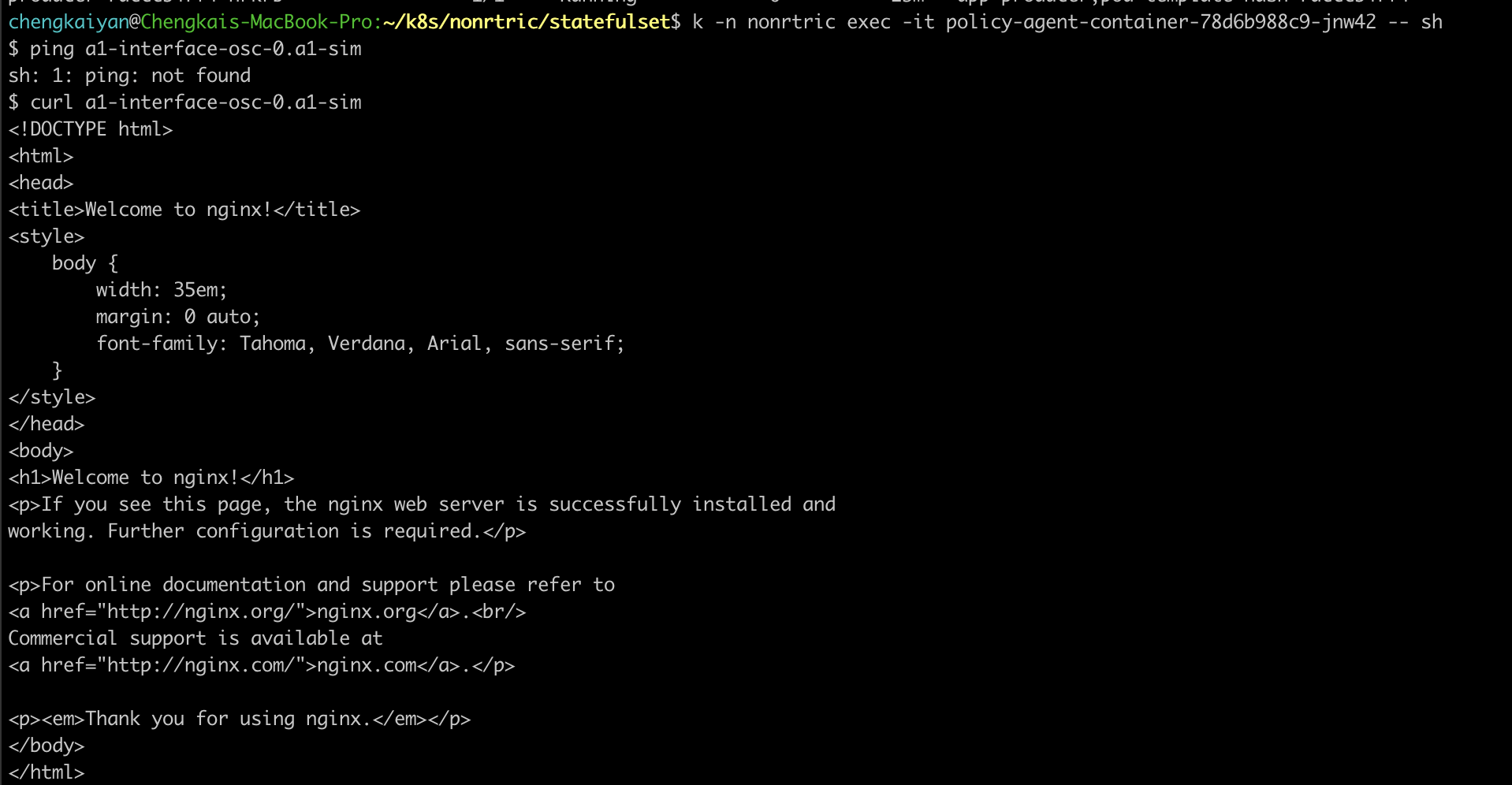
After successfully applying above policy, we login to pod "policy-agent-container-xxxxxx", command:
kubectl -n nonrtric exec -it policy-agent-container-78d6b988c9-jnw42 -- sh curl a1-interface-osc-0.a1-sim
We should be able to see:
If we update labels in the above policy, for exemple:
$ cat <<EOF | kubectl apply -f -
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: nonrtric
spec:
podSelector:
matchLabels:
app: a1-sim
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
app: policy-xxxx-container
- from:
- podSelector:
matchLabels:
app: a1-sim
EOF
After applying this changed policy, we cannot access "a1-sim" endpoints from "policy-agent-container" anymore because the labels do not match.
curl/ping command can no longer reach "a1-sim".