...
The table below lists the CAPIF Core Function APIs that are currently implemented:
Service Name | Service Operations | Operation Semantics | Consumer(s) |
CAPIF_Discover_Service_API | Discover_Service_API | GET /allServiceAPIs | API Invoker, CAPIF core function |
CAPIF_Publish_Service_API | Publish_Service_API | POST /{apfId}//service-apis | API Publishing Function, CAPIF core function |
Unpublish_Service_API | DELETE /{apfId/service-apis/{serviceApiId} | API Publishing Function, CAPIF core function | |
Update_Service_API | PUT /{apfId/service-apis/{serviceApiId} | API Publishing Function, CAPIF core function | |
Get_Service_API | GET /{apfId}/service-apis | API Publishing Function, CAPIF core function | |
CAPIF_API_Invoker_Management_API | Onboard_API_Invoker | POST /onboardedInvokers | API Invoker |
Offboard_API_Invoker | DELETE /onboardedInvokers/{onboardingId} | API Invoker | |
Notify_Onboarding_Completion | Subscribe/Notify | API Invoker | |
Update_API_Invoker_Details | PUT /onboardedInvokers/{onboardingId} | API Invoker | |
Notify_Update_Completion | Subscribe/Notify | API Invoker | |
CAPIF_Security_API | Obtain_Security_Method | PUT /trustedInvokers/{apiInvokerId} | API Invoker |
Obtain_Authorization | POST /securities/{securityId}/token | API Invoker | |
Obtain_API_Invoker_Info | GET /trustedInvokers/{apiInvokerId} | API exposing function | |
Revoke_Authorization | DELETE /trustedInvokers/{apiInvokerId} | API exposing function | |
CAPIF_API_Provider_Management_API | Register_API_Provider | POST /registrations | API Management Function |
Update_API_Provider | PUT /registrations/{registrationId} | API Management Function | |
Deregister_API_Provider | DELETE /registrations/{registrationId} | API Management Function |
Examples to use CAPIF core function APIs
...
More examples can be found in the postman collection below:
Security in CAPIF
Security related information about CAPIF can be found in 3GPP TS 33.122 Security aspects of Common API Framework (CAPIF).
CAPIF establish security requirements for all the interfaces defined in the specification. There are also security requirements that are applicable to all CAPIF entities, such as:
- CAPIF shall provide mechanisms to hide the topology of the PLMN trust domain from the API invokers accessing the service APIs from outside the PLMN trust domain.
- CAPIF shall provide mechanisms to hide the topology of the 3rd party API provider trust domain from the API invokers accessing the service APIs from outside the 3rd party API provider trust domain.
- CAPIF shall provide authorization mechanism for service APIs from the 3rd party API providers.
- CAPIF shall support a common security mechanism for all API implementations to provide confidentiality and integrity protection.
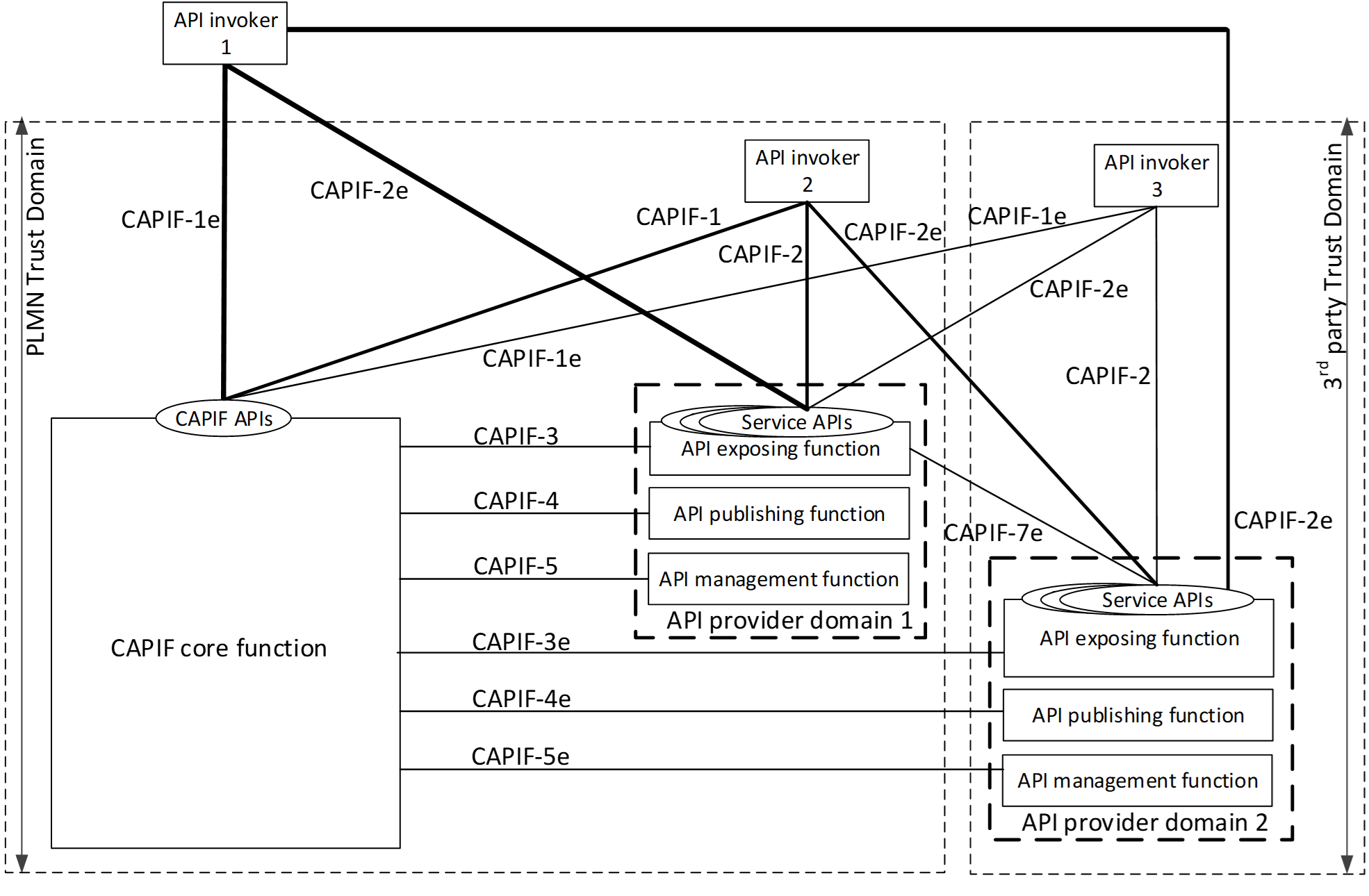
The image below shows the functional security model for CAPIF architecture. CAPIF-1, CAPIF-2, CAPIF-3, CAPIF-4, CAPIF-5 and CAPIF-7 are interfaces that lie within the PLMN trust domain while the CAPIF-1e , CAPIF-2e, CAPIF-3e, CAPIF-4e, CAPIF-5e and CAPIF-7e interfaces are CAPIF core and AEF access points for API Invokers outside of the PLMN trust domain.
Authentication and authorization are required for both API invokers that lie within the PLMN trust domain and API invokers that lie outside of the PLMN trust domain. For an API invoker that is outside of the PLMN trust domain, the CAPIF core function in coordination with the API exposing function utilizes the CAPIF-1e, CAPIF-2e and the CAPIF-3 interfaces to onboard, authenticate and authorize the API invoker prior to granting access to CAPIF services.
Security procedures for API invoker onboarding
The API invoker and the CAPIF core function shall establish a secure session.
With a secure session established, the API Invoker sends an Onboard API Invoker Request message to the CAPIF core function. The Onboard API Invoker Request message carries an onboard credential obtained during pre-provisioning of the onboard enrolment information.
The CAPIF core function shall respond with an Onboard API invoker response message. The response shall include the CAPIF core function assigned API invoker ID, API invoker's certificate and the API invoker Onboard_Secret (generated by the CAPIF core function provided by keycloak).
Security method negotiation
The API invoker and the CAPIF core function shall negotiate a security method that shall be used by the API invoker and the API exposing function for CAPIF-2e interface authentication and protection.
As a pre-condition the API invoker must be onboarded with the CAPIF core function.
After successful mutual authentication on CAPIF-1e interface, the API invoker may send CAPIF-2/2e security capability information to the CAPIF core function in the Security Method Request message, indicating the list of security methods that it supports for each AEF.
The CAPIF core function shall select a security method to be used over CAPIF-2/2e reference point for each requested AEF, taking into account the information sent by the API invoker and send a Security Method Response message to the API invoker indicating the selected security method for each AEF.
Build CAPIF core
Download the following repos:
...
To run the unit tests for the application, run the following command:
| Code Block |
|---|
go test ./... |
The application can also be built as a Docker image, by using the following command. Use the version found in the file container-tag.yaml.
| Code Block |
|---|
docker build -t o-ran-sc/nonrtric-plt-capifcore:<image-version> . |
...