...
cert-manager provides X.509 certificate management on Kubernetes.
Setup
Install
Install cert-manager on your cluster by following the instruction in the link below.
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ kubectl get pods -n cert-manager NAME READY STATUS RESTARTS AGE cert-manager-5b65cb968c-d2zbv 1/1 Running 0 5h46m cert-manager-cainjector-56b88bcdf7-7gbj6 1/1 Running 0 5h46m cert-manager-webhook-c784c79c7-6d57m 1/1 Running 0 5h46m |
Create Issuer
Create a cluster-issuer and a certificate/secret for the self signed root CA
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
apiVersion: cert-manager.io/v1
kind: Issuer
metadata:
name: cm-ca-issuer
namespace: default
spec:
ca:
secretName: cm-cluster-issuer-rootca-secret |
Create Certificate
Create a server key/certificate/keystore/truststore
...
Note: email addresses appear in the subject's alternative name rather than the distinguished name
CA injector
cainjector is used to configure the CA certificates for Mutating Webhooks - see link below.
Kafka
You can use your own certificates and keys with Kafka by adding the following section in your configuration:
| Code Block | ||||
|---|---|---|---|---|
| ||||
clusterCa:
generateCertificateAuthority: false |
If this is set to false you need to setup your own cluster secrets containing the keys and certificates prior to starting the cluster.
Please refer to 8.3. Installing your own CA certificates
You can do the same for the client CA.
For the listeners you can also configure your own server certificates in the brokerCertChainAndKey section.
| Code Block | ||||
|---|---|---|---|---|
| ||||
- name: external
port: 9098
type: nodeport
tls: true
authentication:
type: tls
configuration:
brokerCertChainAndKey:
secretName: cm-kafka-server-certs
certificate: tls.crt
key: tls.key
bootstrap:
alternativeNames:
- localhost
- 192.168.49.2
- my-cluster-kafka-external-bootstrap.kafka
- my-cluster-kafka-external-bootstrap.kafka.svc
- my-cluster-kafka-external-0.kafka
- my-cluster-kafka-external-0.kafka.svc |
Please refer to the brokerCertChainAndKey section in the Strimzi documentation for more information.
Prometheus & Grafana
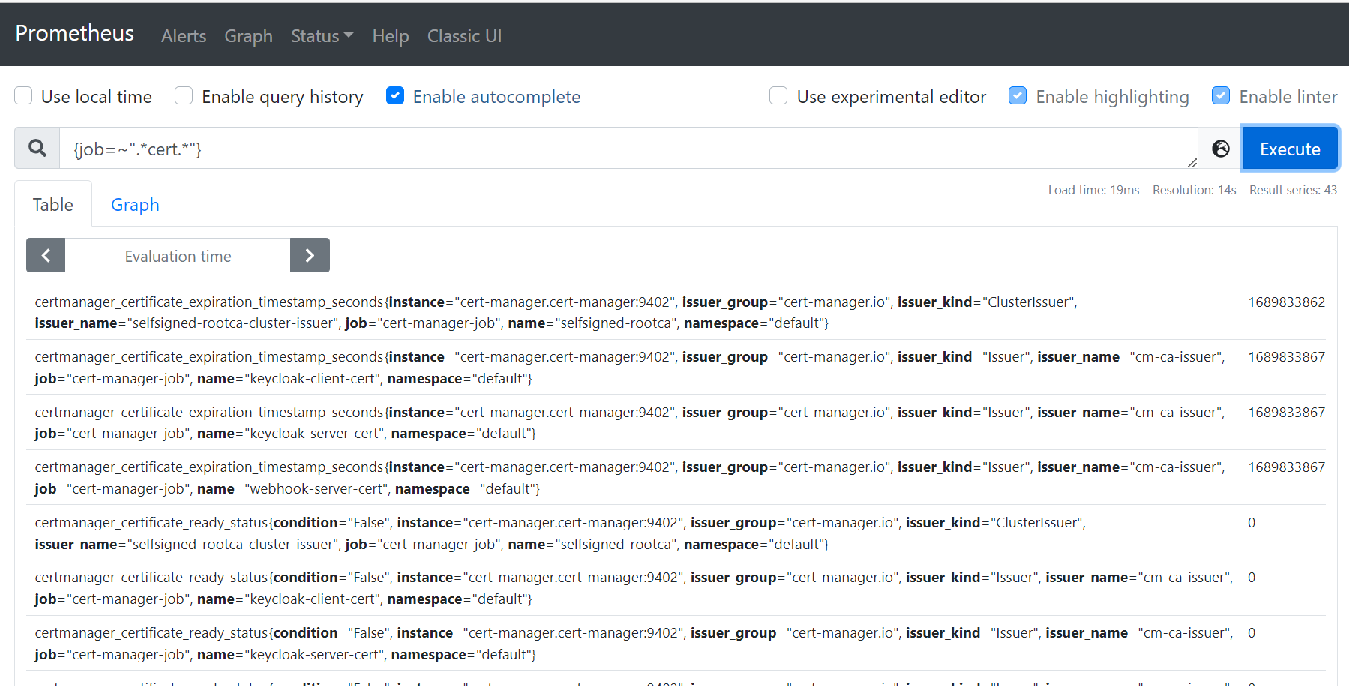
cert-manager provides a metrics endpoint which can be scraped by Prometheus.
| Code Block | ||||
|---|---|---|---|---|
| ||||
scrape_configs:
- job_name: cert-manager-job
metrics_path: /metrics
scheme: http
static_configs:
- targets: ['cert-manager.cert-manager:9402'] |
Once the collection starts you can view these metrics in Prometheus.
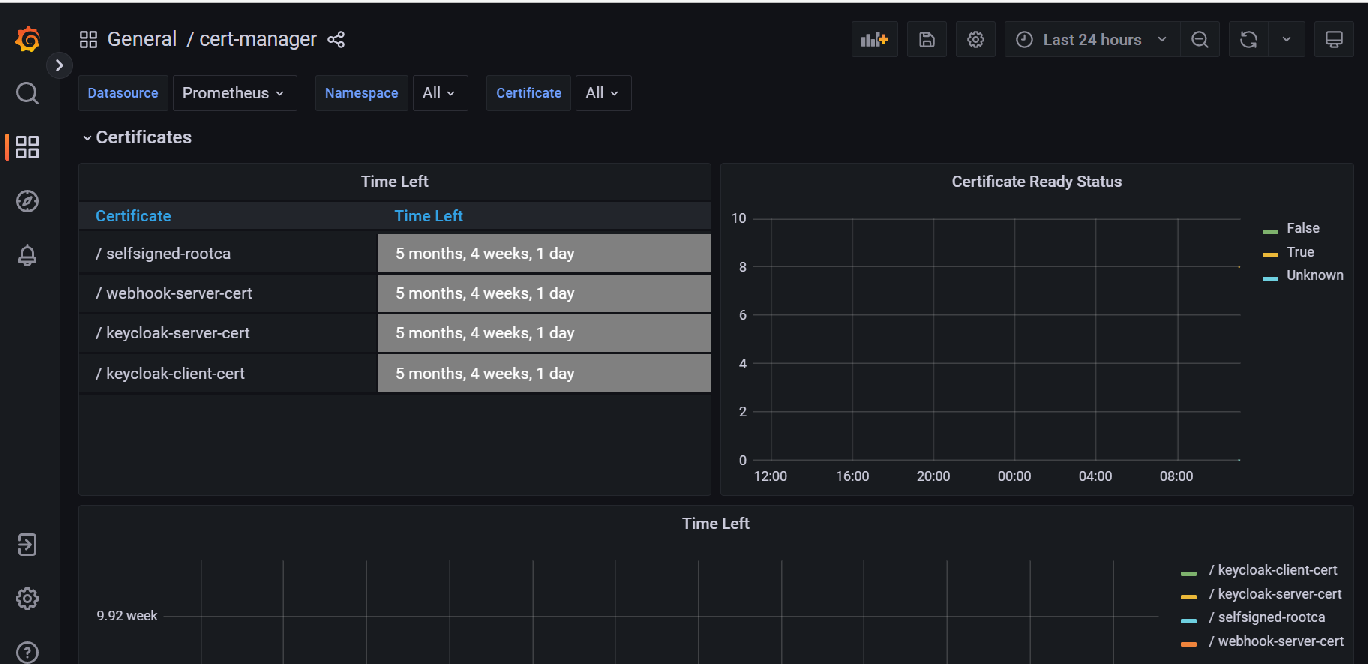
Grafana also provides a dashboard for these metrics: cert-manager dashbord
Links
...