...
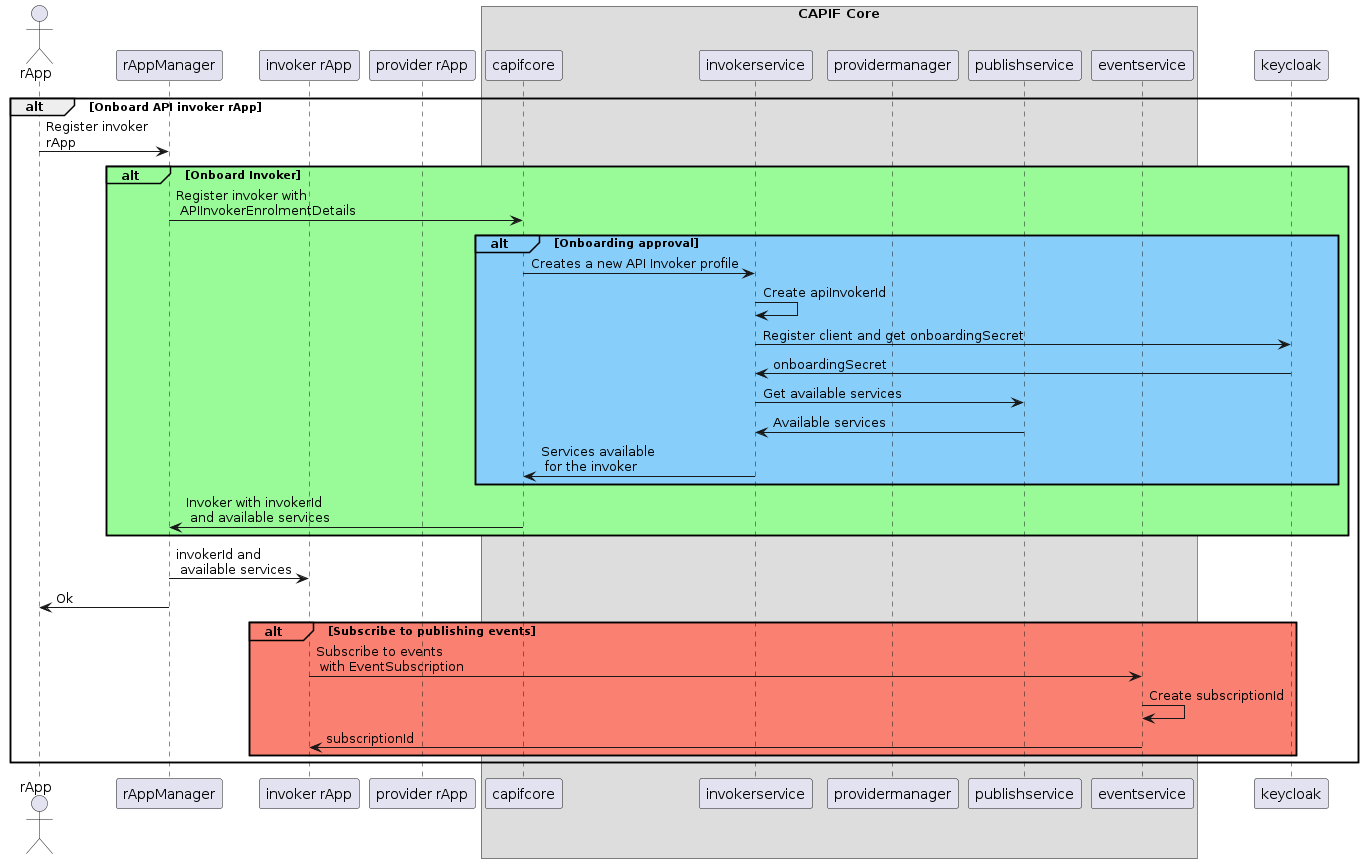
The CAPIF core function shall respond with an Onboard API invoker response message. The response shall include the CAPIF core function assigned API invoker ID, API invoker's certificate and the API invoker Onboard_Secret (generated by the CAPIF core function provided by keycloak).
Security method negotiation
The API invoker and the CAPIF core function shall negotiate a security method that shall be used by the API invoker and the API exposing function for CAPIF-2e interface authentication and protection.
As a pre-condition the API invoker must be onboarded with the CAPIF core function.
After successful mutual authentication on CAPIF-1e interface, the API invoker may send CAPIF-2/2e security capability information to the CAPIF core function in the Security Method Request message, indicating the list of security methods that it supports for each AEF.
The CAPIF core function shall select a security method to be used over CAPIF-2/2e reference point for each requested AEF, taking into account the information sent by the API invoker and send a Security Method Response message to the API invoker indicating the selected security method for each AEF.
Build CAPIF core
| Anchor | ||||
|---|---|---|---|---|
|
Download the following repos:
...
| Code Block |
|---|
docker build -t o-ran-sc/nonrtric-plt-capifcore:<image-version> . |
Run CAPIF core
| Anchor | ||||
|---|---|---|---|---|
|
The CAPIF core needs one configuration file for keycloak including information about keycloak host (url, port and authentication for admin user) and realms. Before using CAPIF API invoker management, an invoker realm must be created in keycloak. Make sure it is created before running CAPIF core. After creating the realm in keycloak, set the name in the keycloak.yaml configuration file.
...